Using Wireshark To Crack Wpa2 With Windows Rating: 6,4/10 8085votes
Using Wireshark To Crack Wpa2 With Windows' title='Using Wireshark To Crack Wpa2 With Windows' />How can I prevent wifi being hacked As usual, Jan beat me with an excellent answer Nevertheless, heres my 2p worth. You CANT make your Wi. Fi network 1. 00 hack proof. Restaurant Accounting Software Programs. Wi. Fi networks are just not that secure, but you can make it more difficult for hackers to break into your network in a number of ways 1. You can crack wifi password easily using your phone through these apps. There are many apps and tools available on the internet but most of them are either fake or. The basic idea is to capture as much encrypted traffic as possible using airodumpng. Each WEP data packet has an associated 3byte Initialization Vector IV after. Instead of using a simple lifetime average, Udemy calculates a courses star rating by considering a number of different factors such as the number of ratings, the. Use WPA2 I suppose if your network only has WPA, youll need to go with that, but thats far from ideal. Use a good password long, mix of upper and lower case letters, digits and special symbols such as spaces, punctuation etc. Without a decent password, there IS no security Change your routers SSID network name to something that will mean something to you, but will not be obvious to anyone passing by one of my clients has named their router upstairs left, which I like. Potentially, hide your SSID when youre done with the setup, as this will make it trickier for potential hackers to know what theyre looking for. You can also set up a whitelist of MAC addresses, allowing only YOUR devices on the network. A MAC address or hardware address is a unique number given to every network card at manufacturing time. It can be simulated, but youd need to know what addresses are allowed before you can do that, thereby making the hackers work harder. Now that your Wi. Fi network is as secure as it can be, you need to secure your computers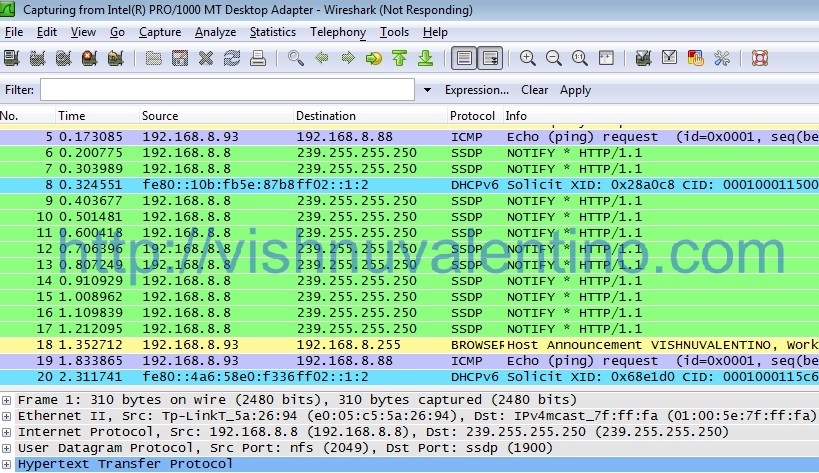 Change your computer login password to a secure password. Make sure you have a decent and up to date antivirus product and an additional anti spywareanti malware product e. Malwarebytes Free from malwarebytes. Scan your hard disc thoroughly with the AV AND anti malware software before proceeding. If you suspect or even feel a little uneasy that your computeraccount was hacked, change all your email and important passwords NOW. Again, use decent passwords, and do not use the same password for different purposes except for low level web sites etc which you dont care about. Importantly, your email password MUST be unique and strong, as so many things hinge on it, including the ability to reset most of your other passwords Make sure that all your email logins are done using encrypted connections e. TLS, SSL. Transmitting a password in the clear, is like shouting it in the middle of a shopping mall, someone is bound to find out about it Finally, most providers on the internet offer additional security measures. Take advantage of that
Change your computer login password to a secure password. Make sure you have a decent and up to date antivirus product and an additional anti spywareanti malware product e. Malwarebytes Free from malwarebytes. Scan your hard disc thoroughly with the AV AND anti malware software before proceeding. If you suspect or even feel a little uneasy that your computeraccount was hacked, change all your email and important passwords NOW. Again, use decent passwords, and do not use the same password for different purposes except for low level web sites etc which you dont care about. Importantly, your email password MUST be unique and strong, as so many things hinge on it, including the ability to reset most of your other passwords Make sure that all your email logins are done using encrypted connections e. TLS, SSL. Transmitting a password in the clear, is like shouting it in the middle of a shopping mall, someone is bound to find out about it Finally, most providers on the internet offer additional security measures. Take advantage of that For example, GMail not only requires encryption HTTPS and SSL, but also offers the option of 2 factor log in, which means that if you log onto a computer you have not used before or not recently, it will send a code to your phone via SMS which you will need to enter before youre allowed into your email. This will stymie most hackers. Using Wireshark To Crack Wpa2 With Windows' title='Using Wireshark To Crack Wpa2 With Windows' />Yahoo have a system whereby you can upload a small picture which will be shown on the screen when you log in. This tells you you really are looking at your Yahoo page, and not a faked one, protecting you from a variety of phishing techniques, including man in the middle attack. As I said above, the key is to use these measures, as they make the hackers life much more difficult. Much like good home security, the bad guys are likely to leave you alone if youre well protectedBuilding and using John the Ripper with MPI support to use multiple CPU cores, maybe across multiple machines, also adding a custom hash type based on MD5 and SHA1. Cracking a wireless network is defeating the security of a wireless localarea network wireless LAN. A commonly used wireless LAN is a WiFi network. Using Wireshark To Crack Wpa2 With Windows' title='Using Wireshark To Crack Wpa2 With Windows' />Cracking of wireless networks Wikipedia. Cracking a wireless network is defeating the security of a wireless local area network wireless LAN. A commonly used wireless LAN is a Wi Fi network. Wireless LANs have inherent security weaknesses from which wired networks are exempt. Wireless cracking is an information network attack similar to a direct intrusion. Two frequent types of vulnerabilities in wireless LANs are those caused by poor configuration, and those caused by weak encryption or flawed security protocols. Wireless network basicseditWireless local area networks are based on IEEE 8. This is a set of standards defined by the Institute of Electrical and Electronics Engineers. By default, people refer to infrastructure networks. Infrastructure networks are composed of one or more access points that coordinate the wireless traffic between the nodes and often connect the nodes to a wired network, acting as a bridge or a router. Each access point constitutes a network that is named a basic service set or BSS. A BSS is identified by a BSSID, usually the MAC address of the access point. Each access point is part of an extended service set or ESS, which is identified by an ESSID or SSID in short, usually a character string. A basic service set consists of one access point and several wireless clients. An extended service set is a configuration with multiple access points and roaming capabilities for the clients. An independent basic service set or IBSS is the ad hoc configuration. This configuration allows wireless clients to connect to each other directly, without an access point as a central manager. Access points broadcast a signal regularly to make the network known to clients. They relay traffic from one wireless client to another. Access points may determine which clients may connect, and when clients do, they are said to be associated with the access point. To obtain access to an access point, both the BSSID and the SSID are required. Ad hoc networks have no access point for central coordination. Each node connects in a peer to peer way. This configuration is an independent basic service set or IBSS. Ad hoc networks also have an SSID. Wireless network framesedit8. Data frames convey the real data, and are similar to those of Ethernet. Management frames maintain both network configuration and connectivity. Control frames manage access to the ether and prevent access points and clients from interfering with each other in the ether. Some information on management frames will be helpful to better understand what programs for reconnaissance do. Beacon frames are used primarily in reconnaissance. They advertise the existence and basic configuration of the network. Each frame contains the BSSID, the SSID, and some information on basic authentication and encryption. Clients use the flow of beacon frames to monitor the signal strength of their access point. Probe request frames are almost the same as the beacon frames. A probe request frame is sent from a client when it wants to connect to a wireless network. It contains information about the requested network. Probe response frames are sent to clients to answer probe request frames. One response frame answers each request frame, and it contains information on the capabilities and configurations of the network. Useful for reconnaissance. Authentication request frames are sent by clients when they want to connect to a network. Authentication precedes association in infrastructure networks. Either open authentication or shared key authentication is possible. After serious flaws were found in shared key authentication, most networks switched to open authentication, combined with a stronger authentication method applied after the association phase. Authentication response frames are sent to clients to answer authentication request frames. There is one answer to each request, and it contains either status information or a challenge related to shared key authentication. Association request frames are sent by clients to associate with the network. An association request frame contains much of the same information as the probe request contains, and it must have the SSID. This can be used to obtain the SSID when a network is configured to hide the SSID in beacon frames. Association response frames are sent to clients to answer an association request frame. They contain a bit of network information and indicate whether the association was successful. Deauthentication and disassociation frames are sent to a node to notify that an authentication or an association has failed and must be established anew. Reconnaissance of wireless networkseditWardriving is a common method of wireless network reconnaissance. A well equipped wardriver uses a laptop computer with a wireless card, an antenna mounted on the car, a power inverter, a connected GPS receiver, and can connect to the internet wirelessly. The purpose of wardriving is to locate a wireless network and to collect information about its configuration and associated clients. The laptop computer and the wireless card must support a mode called monitor or rfmon. NetstumblereditNetstumbler is a network discovery program for Windows. It is free. Netstumbler has become one of the most popular programs for wardriving and wireless reconnaissance, although it has a disadvantage. It can be detected easily by most wireless intrusion detection systems, because it actively probes a network to collect information. Netstumbler has integrated support for a GPS unit. With this support, Netstumbler displays GPS coordinate information next to the information about each discovered network, which can be useful for finding specific networks again after having sorted out collected data. The latest release of Netstumbler is of 1 April 2. It does not work well with 6. Windows XP or Windows Vista. SSIDer is a Wi Fi network scanner for the 3. Windows XP, Vista, 7, Windows 8 and Android. It is free and open source. The software uses the current wireless card or a wireless USB adapter and supports most GPS devices namely those that use NMEA 2. Its graphical user interface shows MAC address, SSID, signal strength, hardware brand, security, and network type of nearby Wi Fi networks. It can also track the strength of the signals and show them in a time graph. Kismet is a wireless network traffic analyser for OS X, Linux, Open. BSD, Net. BSD, and Free. Crack File For Age Of Empires 2. BSD. It is free and open source. Kismet has become the most popular program for serious wardrivers. It offers a rich set of features, including deep analysis of captured traffic. WiresharkeditWireshark is a packet sniffer and network traffic analyser that can run on all popular operating systems, but support for the capture of wireless traffic is limited. It is free and open source. Decoding and analysing wireless traffic is not the foremost function of Wireshark, but it can give results that cannot be obtained with other programs. Wireshark requires sufficient knowledge of the network protocols to obtain a full analysis of the traffic, however. Analysers of Air. MagneteditAir. Magnet Laptop Analyser and Air. Magnet Handheld Analyser are wireless network analysis tools made by Air. Magnet. The company started with the Handheld Analyser, which was very suitable for surveying sites where wireless networks were deployed as well as for finding rogue access points.
For example, GMail not only requires encryption HTTPS and SSL, but also offers the option of 2 factor log in, which means that if you log onto a computer you have not used before or not recently, it will send a code to your phone via SMS which you will need to enter before youre allowed into your email. This will stymie most hackers. Using Wireshark To Crack Wpa2 With Windows' title='Using Wireshark To Crack Wpa2 With Windows' />Yahoo have a system whereby you can upload a small picture which will be shown on the screen when you log in. This tells you you really are looking at your Yahoo page, and not a faked one, protecting you from a variety of phishing techniques, including man in the middle attack. As I said above, the key is to use these measures, as they make the hackers life much more difficult. Much like good home security, the bad guys are likely to leave you alone if youre well protectedBuilding and using John the Ripper with MPI support to use multiple CPU cores, maybe across multiple machines, also adding a custom hash type based on MD5 and SHA1. Cracking a wireless network is defeating the security of a wireless localarea network wireless LAN. A commonly used wireless LAN is a WiFi network. Using Wireshark To Crack Wpa2 With Windows' title='Using Wireshark To Crack Wpa2 With Windows' />Cracking of wireless networks Wikipedia. Cracking a wireless network is defeating the security of a wireless local area network wireless LAN. A commonly used wireless LAN is a Wi Fi network. Wireless LANs have inherent security weaknesses from which wired networks are exempt. Wireless cracking is an information network attack similar to a direct intrusion. Two frequent types of vulnerabilities in wireless LANs are those caused by poor configuration, and those caused by weak encryption or flawed security protocols. Wireless network basicseditWireless local area networks are based on IEEE 8. This is a set of standards defined by the Institute of Electrical and Electronics Engineers. By default, people refer to infrastructure networks. Infrastructure networks are composed of one or more access points that coordinate the wireless traffic between the nodes and often connect the nodes to a wired network, acting as a bridge or a router. Each access point constitutes a network that is named a basic service set or BSS. A BSS is identified by a BSSID, usually the MAC address of the access point. Each access point is part of an extended service set or ESS, which is identified by an ESSID or SSID in short, usually a character string. A basic service set consists of one access point and several wireless clients. An extended service set is a configuration with multiple access points and roaming capabilities for the clients. An independent basic service set or IBSS is the ad hoc configuration. This configuration allows wireless clients to connect to each other directly, without an access point as a central manager. Access points broadcast a signal regularly to make the network known to clients. They relay traffic from one wireless client to another. Access points may determine which clients may connect, and when clients do, they are said to be associated with the access point. To obtain access to an access point, both the BSSID and the SSID are required. Ad hoc networks have no access point for central coordination. Each node connects in a peer to peer way. This configuration is an independent basic service set or IBSS. Ad hoc networks also have an SSID. Wireless network framesedit8. Data frames convey the real data, and are similar to those of Ethernet. Management frames maintain both network configuration and connectivity. Control frames manage access to the ether and prevent access points and clients from interfering with each other in the ether. Some information on management frames will be helpful to better understand what programs for reconnaissance do. Beacon frames are used primarily in reconnaissance. They advertise the existence and basic configuration of the network. Each frame contains the BSSID, the SSID, and some information on basic authentication and encryption. Clients use the flow of beacon frames to monitor the signal strength of their access point. Probe request frames are almost the same as the beacon frames. A probe request frame is sent from a client when it wants to connect to a wireless network. It contains information about the requested network. Probe response frames are sent to clients to answer probe request frames. One response frame answers each request frame, and it contains information on the capabilities and configurations of the network. Useful for reconnaissance. Authentication request frames are sent by clients when they want to connect to a network. Authentication precedes association in infrastructure networks. Either open authentication or shared key authentication is possible. After serious flaws were found in shared key authentication, most networks switched to open authentication, combined with a stronger authentication method applied after the association phase. Authentication response frames are sent to clients to answer authentication request frames. There is one answer to each request, and it contains either status information or a challenge related to shared key authentication. Association request frames are sent by clients to associate with the network. An association request frame contains much of the same information as the probe request contains, and it must have the SSID. This can be used to obtain the SSID when a network is configured to hide the SSID in beacon frames. Association response frames are sent to clients to answer an association request frame. They contain a bit of network information and indicate whether the association was successful. Deauthentication and disassociation frames are sent to a node to notify that an authentication or an association has failed and must be established anew. Reconnaissance of wireless networkseditWardriving is a common method of wireless network reconnaissance. A well equipped wardriver uses a laptop computer with a wireless card, an antenna mounted on the car, a power inverter, a connected GPS receiver, and can connect to the internet wirelessly. The purpose of wardriving is to locate a wireless network and to collect information about its configuration and associated clients. The laptop computer and the wireless card must support a mode called monitor or rfmon. NetstumblereditNetstumbler is a network discovery program for Windows. It is free. Netstumbler has become one of the most popular programs for wardriving and wireless reconnaissance, although it has a disadvantage. It can be detected easily by most wireless intrusion detection systems, because it actively probes a network to collect information. Netstumbler has integrated support for a GPS unit. With this support, Netstumbler displays GPS coordinate information next to the information about each discovered network, which can be useful for finding specific networks again after having sorted out collected data. The latest release of Netstumbler is of 1 April 2. It does not work well with 6. Windows XP or Windows Vista. SSIDer is a Wi Fi network scanner for the 3. Windows XP, Vista, 7, Windows 8 and Android. It is free and open source. The software uses the current wireless card or a wireless USB adapter and supports most GPS devices namely those that use NMEA 2. Its graphical user interface shows MAC address, SSID, signal strength, hardware brand, security, and network type of nearby Wi Fi networks. It can also track the strength of the signals and show them in a time graph. Kismet is a wireless network traffic analyser for OS X, Linux, Open. BSD, Net. BSD, and Free. Crack File For Age Of Empires 2. BSD. It is free and open source. Kismet has become the most popular program for serious wardrivers. It offers a rich set of features, including deep analysis of captured traffic. WiresharkeditWireshark is a packet sniffer and network traffic analyser that can run on all popular operating systems, but support for the capture of wireless traffic is limited. It is free and open source. Decoding and analysing wireless traffic is not the foremost function of Wireshark, but it can give results that cannot be obtained with other programs. Wireshark requires sufficient knowledge of the network protocols to obtain a full analysis of the traffic, however. Analysers of Air. MagneteditAir. Magnet Laptop Analyser and Air. Magnet Handheld Analyser are wireless network analysis tools made by Air. Magnet. The company started with the Handheld Analyser, which was very suitable for surveying sites where wireless networks were deployed as well as for finding rogue access points.