Driver Toolkit Registry Key Rating: 10,0/10 2881votes
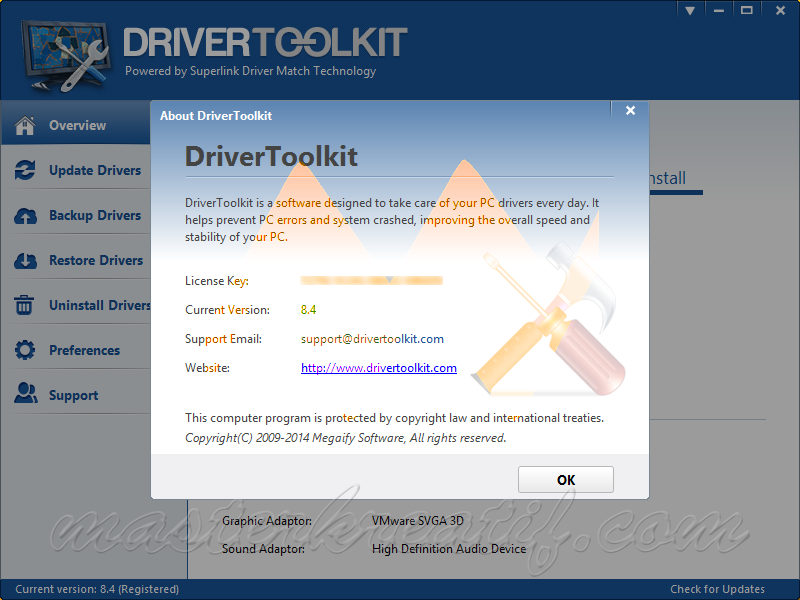
Windows Registry Wikipedia. The registry is a hierarchical database that stores low level settings for the Microsoft Windows operating system and for applications that opt to use the registry. The kernel, device drivers, services, Security Accounts Manager SAM, and user interface can all use the registry. The registry also allows access to counters for profiling system performance. In simple terms, the registry or Windows Registry contains information, settings, options, and other values for programs and hardware installed on all versions of Microsoft Windows operating systems. For example, when a program is installed, a new subkey containing settings like a programs location, its version, and how to start the program, are all added to the Windows Registry. When introduced with Windows 3. Windows Registry primarily stored configuration information for COM based components. Windows 9. 5 and Windows NT extended its use to rationalise and centralise the information in the profusion of INI files, which held the configurations for individual programs, and were stored at various locations. It is not a requirement for Windows applications to use the Windows Registry. Driver_Detective1.jpg' alt='Driver Toolkit Registry Key' title='Driver Toolkit Registry Key' />For example,. NET Framework applications use XML files for configuration, while portable applications usually keep their configuration files with their executables. RationaleeditPrior to the Windows Registry,. INI files stored each programs settings as a text file, often located in a shared location that did not provide user specific settings in a multi user scenario. By contrast, the Windows Registry stores all application settings in one logical repository but a number of discrete files and in a standardized form. According to Microsoft, this offers several advantages over. INI files. 23 Since file parsing is done much more efficiently with a binary format, it may be read from or written to more quickly than an INI file. As well, strongly typed data can be stored in the registry, as opposed to the text information stored in. Twobranch independent employing just 12 staff is assured of 10,000 new sales instructions. Continue Reading. Rationale. Prior to the Windows Registry. INI files stored each programs settings as a text file, often located in a shared location that did not provide user. The Christmas Registry provides a listing of supports available in the City of Hamilton to help ensure as many people as possible will be able to enjoy Christmas. It. 
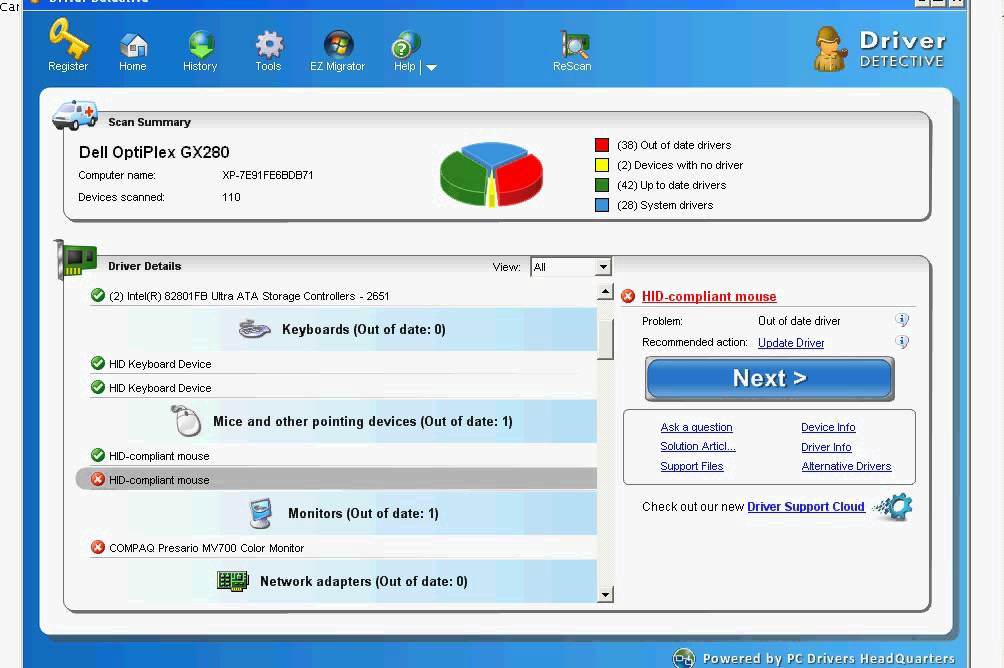 Webopedias list of Data File Formats and File Extensions makes it easy to look through thousands of extensions and file formats to find what you need. SmartPCFixer is a fully featured and easytouse system optimization suite. With it, you can clean windows registry, remove cache files, fix errors, defrag disk. MS Office 2016 Product key, Keygen included can now be downloaded from this page. You can either use License key or Keygen to activate MS Office 2016 easily without a. This article includes a list of references, but its sources remain unclear because it has insufficient inline citations. Please help to improve this article by. Modern Driver Management Modern Driver Management not to be confused with MDM, mobile device management combines new methods for driver management by. INI files. This is a benefit when editing keys manually using regedit. Windows Registry Editor. Because user based registry settings are loaded from a user specific path rather than from a read only system location, the registry allows multiple users to share the same machine, and also allows programs to work for less privileged users. Backup and restoration is also simplified as the registry can be accessed over a network connection for remote managementsupport, including from scripts, using the standard set of APIs, as long as the Remote Registry service is running and firewall rules permit this. Because the registry is a database, it offers improved system integrity with features such as atomic updates. Pdf Split And Merge Ubuntu more. If two processes attempt to update the same registry value at the same time, one processs change will precede the others and the overall consistency of the data will be maintained. Where changes are made to. INI files, such race conditions can result in inconsistent data that does not match either attempted update. Download tools to clean, optimize, backup or compress your registry. A crossplatform C based Toolkit for developing GUIs easily and effectively UnixX,Win32. Open source, LGPL. Windows Vista and later operating systems provide transactional updates to the registry by means of the Kernel Transaction Manager, extending the atomicity guarantees across multiple key andor value changes, with traditional commitabort semantics. Note however that NTFS provides such support for the file system as well, so the same guarantees could, in theory, be obtained with traditional configuration files. StructureeditKeys and valueseditThe registry contains two basic elements keys and values. Registry keys are container objects similar to folders. Registry values are non container objects similar to files. Keys may contain values and subkeys. Keys are referenced with a syntax similar to Windows path names, using backslashes to indicate levels of hierarchy. Keys must have a case insensitive name without backslashes. The hierarchy of registry keys can only be accessed from a known root key handle which is anonymous but whose effective value is a constant numeric handle that is mapped to the content of a registry key preloaded by the kernel from a stored hive, or to the content of a subkey within another root key, or mapped to a registered service or DLL that provides access to its contained subkeys and values. E. g. HKEYLOCALMACHINESoftwareMicrosoftWindows refers to the subkey Windows of the subkey Microsoft of the subkey Software of the HKEYLOCALMACHINE root key. There are seven predefined root keys, traditionally named according to their constant handles defined in the Win. API, or by synonymous abbreviations depending on applications HKEYLOCALMACHINE or HKLMHKEYCURRENTCONFIG or HKCCHKEYCLASSESROOT or HKCRHKEYCURRENTUSER or HKCUHKEYUSERS or HKUHKEYPERFORMANCEDATA only in Windows NT, but invisible in the Windows Registry EditorHKEYDYNDATA only in Windows 9x, and visible in the Windows Registry EditorLike other files and services in Windows, all registry keys may be restricted by access control lists ACLs, depending on user privileges, or on security tokens acquired by applications, or on system security policies enforced by the system these restrictions may be predefined by the system itself, and configured by local system administrators or by domain administrators. Different users, programs, services or remote systems may only see some parts of the hierarchy or distinct hierarchies from the same root keys. Registry values are namedata pairs stored within keys. Registry values are referenced separately from registry keys. Each registry value stored in a registry key has a unique name whose letter case is not significant. The Windows API functions that query and manipulate registry values take value names separately from the key path andor handle that identifies the parent key. Registry values may contain backslashes in their names, but doing so makes them difficult to distinguish from their key paths when using some legacy Windows Registry API functions whose usage is deprecated in Win. The terminology is somewhat misleading, as each registry key is similar to an associative array, where standard terminology would refer to the name part of each registry value as a key. The terms are a holdout from the 1. Windows 3, in which registry keys could not contain arbitrary namedata pairs, but rather contained only one unnamed value which had to be a string. In this sense, the entire registry was like a single associative array where the registry keys in both the registry sense and dictionary sense formed a hierarchy, and the registry values were all strings. When the 3. 2 bit registry was created, so was the additional capability of creating multiple named values per key, and the meanings of the names were somewhat distorted. For compatibility with the previous behavior, each registry key may have a default value, whose name is the empty string. Each value can store arbitrary data with variable length and encoding, but which is associated with a symbolic type defined as a numeric constant defining how to parse this data. The standard types are List of standard registry value types. Bernina Serial Numbers. Type IDSymbolic type name. Meaning and encoding of the data stored in the registry value. REGNONENo type the stored value, if any1. REGSZA string value, normally stored and exposed in UTF 1. LE when using the Unicode version of Win. API functions, usually terminated by a NUL character. Microsoft Deployment Toolkit Wikipedia. Microsoft Deployment Toolkit MDT formerly Business Desktop Deployment2 is a computer program that permits network deployment of Microsoft Windows and Microsoft Office. OvervieweditMDT can help build an automated installation source for deploying Windows operating systems from Windows 7 and Windows Server 2. Windows Deployment Services WDS or System Center Configuration Manager SCCM. Device drivers, Windows updates and software can be included with the build. All the software intended for installation Operating System, drivers, updates and applications are added to a pool of available software and packaged into deployment packages. The Operating System and drivers to be included with this package are selected, and the administrator password, owner information, and product key are specified. Microsoft Deployment Toolkit generates a custom Windows PEPreinstallation Environment image that allows client machines to install the assembled deployment packages over the network from the MDT server. This Windows PE disk image can be burned to and booted from a CD, or booted with Windows Deployment Services. When selecting the package to deploy, software that has been included in the pool may also be selected for installation. OperationeditThe Microsoft Deployment Toolkit MDT supports three types of deployments 3 Zero Touch Installation ZTI, Lite Touch Installation LTI, and User Driven Installation UDI. ZTI is a fully automated deployment scheme in which installation requires no user interaction whatsoever. UDI deployments require full manual intervention to respond to every installation prompt, such as machine name, password or language setting. ZTI and UDI deployments both require a Microsoft System Center infrastructure. ZTI deployments require a persistent network connection to the distribution point. LTI deployments require limited user interaction. An LTI deployment needs very little infrastructure, so it can be installed from a network share, or media using either a USB flash drive or an optical disc. See alsoeditReferenceseditHow to Install ADK and MDT on Windows Server 2. External linkseditMicrosoft deployment resources.
Webopedias list of Data File Formats and File Extensions makes it easy to look through thousands of extensions and file formats to find what you need. SmartPCFixer is a fully featured and easytouse system optimization suite. With it, you can clean windows registry, remove cache files, fix errors, defrag disk. MS Office 2016 Product key, Keygen included can now be downloaded from this page. You can either use License key or Keygen to activate MS Office 2016 easily without a. This article includes a list of references, but its sources remain unclear because it has insufficient inline citations. Please help to improve this article by. Modern Driver Management Modern Driver Management not to be confused with MDM, mobile device management combines new methods for driver management by. INI files. This is a benefit when editing keys manually using regedit. Windows Registry Editor. Because user based registry settings are loaded from a user specific path rather than from a read only system location, the registry allows multiple users to share the same machine, and also allows programs to work for less privileged users. Backup and restoration is also simplified as the registry can be accessed over a network connection for remote managementsupport, including from scripts, using the standard set of APIs, as long as the Remote Registry service is running and firewall rules permit this. Because the registry is a database, it offers improved system integrity with features such as atomic updates. Pdf Split And Merge Ubuntu more. If two processes attempt to update the same registry value at the same time, one processs change will precede the others and the overall consistency of the data will be maintained. Where changes are made to. INI files, such race conditions can result in inconsistent data that does not match either attempted update. Download tools to clean, optimize, backup or compress your registry. A crossplatform C based Toolkit for developing GUIs easily and effectively UnixX,Win32. Open source, LGPL. Windows Vista and later operating systems provide transactional updates to the registry by means of the Kernel Transaction Manager, extending the atomicity guarantees across multiple key andor value changes, with traditional commitabort semantics. Note however that NTFS provides such support for the file system as well, so the same guarantees could, in theory, be obtained with traditional configuration files. StructureeditKeys and valueseditThe registry contains two basic elements keys and values. Registry keys are container objects similar to folders. Registry values are non container objects similar to files. Keys may contain values and subkeys. Keys are referenced with a syntax similar to Windows path names, using backslashes to indicate levels of hierarchy. Keys must have a case insensitive name without backslashes. The hierarchy of registry keys can only be accessed from a known root key handle which is anonymous but whose effective value is a constant numeric handle that is mapped to the content of a registry key preloaded by the kernel from a stored hive, or to the content of a subkey within another root key, or mapped to a registered service or DLL that provides access to its contained subkeys and values. E. g. HKEYLOCALMACHINESoftwareMicrosoftWindows refers to the subkey Windows of the subkey Microsoft of the subkey Software of the HKEYLOCALMACHINE root key. There are seven predefined root keys, traditionally named according to their constant handles defined in the Win. API, or by synonymous abbreviations depending on applications HKEYLOCALMACHINE or HKLMHKEYCURRENTCONFIG or HKCCHKEYCLASSESROOT or HKCRHKEYCURRENTUSER or HKCUHKEYUSERS or HKUHKEYPERFORMANCEDATA only in Windows NT, but invisible in the Windows Registry EditorHKEYDYNDATA only in Windows 9x, and visible in the Windows Registry EditorLike other files and services in Windows, all registry keys may be restricted by access control lists ACLs, depending on user privileges, or on security tokens acquired by applications, or on system security policies enforced by the system these restrictions may be predefined by the system itself, and configured by local system administrators or by domain administrators. Different users, programs, services or remote systems may only see some parts of the hierarchy or distinct hierarchies from the same root keys. Registry values are namedata pairs stored within keys. Registry values are referenced separately from registry keys. Each registry value stored in a registry key has a unique name whose letter case is not significant. The Windows API functions that query and manipulate registry values take value names separately from the key path andor handle that identifies the parent key. Registry values may contain backslashes in their names, but doing so makes them difficult to distinguish from their key paths when using some legacy Windows Registry API functions whose usage is deprecated in Win. The terminology is somewhat misleading, as each registry key is similar to an associative array, where standard terminology would refer to the name part of each registry value as a key. The terms are a holdout from the 1. Windows 3, in which registry keys could not contain arbitrary namedata pairs, but rather contained only one unnamed value which had to be a string. In this sense, the entire registry was like a single associative array where the registry keys in both the registry sense and dictionary sense formed a hierarchy, and the registry values were all strings. When the 3. 2 bit registry was created, so was the additional capability of creating multiple named values per key, and the meanings of the names were somewhat distorted. For compatibility with the previous behavior, each registry key may have a default value, whose name is the empty string. Each value can store arbitrary data with variable length and encoding, but which is associated with a symbolic type defined as a numeric constant defining how to parse this data. The standard types are List of standard registry value types. Bernina Serial Numbers. Type IDSymbolic type name. Meaning and encoding of the data stored in the registry value. REGNONENo type the stored value, if any1. REGSZA string value, normally stored and exposed in UTF 1. LE when using the Unicode version of Win. API functions, usually terminated by a NUL character. Microsoft Deployment Toolkit Wikipedia. Microsoft Deployment Toolkit MDT formerly Business Desktop Deployment2 is a computer program that permits network deployment of Microsoft Windows and Microsoft Office. OvervieweditMDT can help build an automated installation source for deploying Windows operating systems from Windows 7 and Windows Server 2. Windows Deployment Services WDS or System Center Configuration Manager SCCM. Device drivers, Windows updates and software can be included with the build. All the software intended for installation Operating System, drivers, updates and applications are added to a pool of available software and packaged into deployment packages. The Operating System and drivers to be included with this package are selected, and the administrator password, owner information, and product key are specified. Microsoft Deployment Toolkit generates a custom Windows PEPreinstallation Environment image that allows client machines to install the assembled deployment packages over the network from the MDT server. This Windows PE disk image can be burned to and booted from a CD, or booted with Windows Deployment Services. When selecting the package to deploy, software that has been included in the pool may also be selected for installation. OperationeditThe Microsoft Deployment Toolkit MDT supports three types of deployments 3 Zero Touch Installation ZTI, Lite Touch Installation LTI, and User Driven Installation UDI. ZTI is a fully automated deployment scheme in which installation requires no user interaction whatsoever. UDI deployments require full manual intervention to respond to every installation prompt, such as machine name, password or language setting. ZTI and UDI deployments both require a Microsoft System Center infrastructure. ZTI deployments require a persistent network connection to the distribution point. LTI deployments require limited user interaction. An LTI deployment needs very little infrastructure, so it can be installed from a network share, or media using either a USB flash drive or an optical disc. See alsoeditReferenceseditHow to Install ADK and MDT on Windows Server 2. External linkseditMicrosoft deployment resources.